Here is a guide to the strace utility, rewritten from the provided text to be original, engaging, and formatted for your website.
Table of Contents
- 1. Debugging the Undebuggable: A Practical Guide to Strace in Linux
- 2. Scenario 1: The Case of the Missing File 📂
- 2.1 The Problem
- 2.2 The Investigation
- 2.3 The Insight
- 3. Scenario 2: Unmasking Memory Allocation Failures 💾
- 3.1 The Problem
- 3.2 The Investigation
- 3.3 The Insight
- 4. Scenario 3: Solving a Permission Puzzle 🔐
- 4.1 The Problem
- 4.2 The Investigation
- 4.3 The Insight
- 5. Scenario 4: Profiling Performance Bottlenecks 🚀
- 5.1 The Problem
- 5.2 The Investigation
- 5.3 The Insight
- 6. Best Practices and Next Steps
Debugging the Undebuggable: A Practical Guide to Strace in Linux
If you’ve worked on Linux, you’ve hit “the wall.” It’s that moment when an application crashes with a vague error, a network connection mysteriously drops, or performance grinds to a halt for no obvious reason. These are the problems that traditional logging can’t solve, and they can burn hours of your time.
When you hit this wall, you need to go deeper—to the level of system calls. System calls are the fundamental way your applications interact with the Linux kernel to do things like read files, allocate memory, or open network connections. strace is a powerful utility that lets you listen in on this conversation, showing you exactly what your program is asking the kernel to do and how the kernel is responding. 🕵️♀️
This guide will walk you through four practical, real-world scenarios to show you how strace can turn a mysterious problem into a clear solution.
Scenario 1: The Case of the Missing File 📂
One of the most common headaches is an application failing because it can’t find a file. The error message might be clear, but in complex applications with tangled dependencies, you might not even know which file is missing.
The Problem
Let’s imagine a simple Python script that tries to open a file that doesn’t exist:
Python
# missing_file.py
def main():
try:
with open('/tmp/does-not-exist.txt', 'r') as f:
print("File opened successfully")
except FileNotFoundError as e:
print(f"Failed to open file: {e}")
if __name__ == "__main__":
main()
The Investigation
Running this script with strace is simple. You just prepend strace to your normal command:
$ strace python3 missing_file.py
As strace logs every system call, you’ll see a lot of output. But the crucial line will jump out at you:
openat(AT_FDCWD, "/tmp/does-not-exist.txt", O_RDONLY|O_CLOEXEC) = -1 ENOENT (No such file or directory)
The Insight
Let’s break this down:
openat(...): This is the system call your script used to try and open a file."/tmp/does-not-exist.txt": This is the exact path of the file it was looking for. No ambiguity.= -1 ENOENT (No such file or directory): This is the kernel’s response. The-1indicates an error, andENOENTis the error code.stracehelpfully translates this for you.
With this single line, strace has pinpointed the exact file path that caused the failure, allowing you to fix incorrect paths, check working directories, or resolve installation issues.
Scenario 2: Unmasking Memory Allocation Failures 💾
Memory issues are notoriously difficult to diagnose. An “out-of-memory” error is one thing, but sometimes an application fails silently or behaves erratically when a memory request is denied by the kernel.
The Problem
This script attempts to allocate a massive 4GB of memory, which is likely to fail on most systems:
Python
# memory_issue.py
def main():
try:
size = 1024 * 1024 * 1024 * 4 # 4GB
print(f"Attempting to allocate {size} bytes")
large_array = bytearray(size)
print("Memory allocated successfully")
except MemoryError as e:
print(f"Memory allocation failed: {e}")
if __name__ == "__main__":
main()
The Investigation
The output of strace can be overwhelming, so it’s best to filter for only the system calls you care about. For memory, we’re interested in brk, mmap, and munmap. We can use the -e flag to specify this:
$ strace -e trace=brk,mmap,munmap python3 memory_issue.py
When the allocation fails, you’ll see a clear message in the output:
mmap(NULL, 4294967296, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = -1 ENOMEM (Cannot allocate memory)
The Insight
The kernel’s response ENOMEM (Error Number: Out of Memory) tells you everything. The application requested a huge chunk of memory with the mmap system call, and the kernel denied it. Now you have a concrete starting point: you can either reduce the application’s memory footprint or investigate why the system has insufficient available memory.
Scenario 3: Solving a Permission Puzzle 🔐
Sometimes the file is there, the path is correct, but your application still fails. This is often a classic case of incorrect file permissions.
The Problem
This script attempts to read a file that our current user doesn’t have permission to access:
Python
# permission_issue.py
def main():
try:
with open('/tmp/no-permission.txt', 'r') as f:
print("File opened successfully")
except PermissionError as e:
print(f"Failed to open file: {e}")
if __name__ == "__main__":
main()
To set up this scenario, we create a file owned by root with restricted permissions:
Bash
$ sudo bash -c 'echo "Secret data" > /tmp/no-permission.txt'
$ sudo chown root /tmp/no-permission.txt
$ sudo chmod 600 /tmp/no-permission.txt
The Investigation
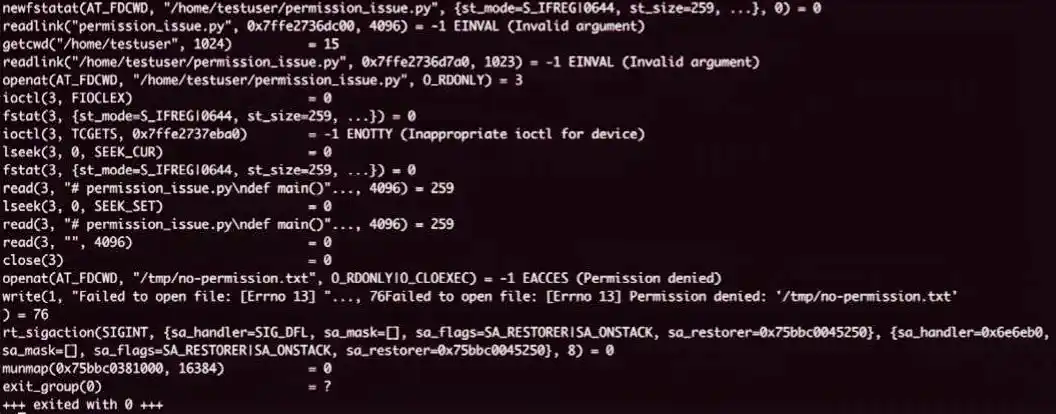
Running the script with strace reveals the problem instantly:
$ strace python3 permission_issue.py
The key line in the output will be:
openat(AT_FDCWD, "/tmp/no-permission.txt", O_RDONLY|O_CLOEXEC) = -1 EACCES (Permission denied)
The Insight
Just like before, strace shows the openat call, but this time the kernel’s response is different. The error code EACCES (Error: Access Denied) confirms that the issue isn’t a missing file but a permissions barrier. You now know exactly which file is causing the problem and can use ls -l to check its ownership and permissions.
Scenario 4: Profiling Performance Bottlenecks 🚀
Performance issues can often be traced back to inefficient patterns of system calls. An application might be making thousands of tiny file reads instead of a few large ones, creating significant overhead. strace can help you spot these inefficiencies.
The Problem
The following script reads 10,000 bytes from a file, but it does so in the most inefficient way possible: one byte at a time.
Python
# io_profile.py
import os
def main():
# Create a 10MB test file
os.system("dd if=/dev/urandom of=/tmp/test_file bs=1M count=10 >/dev/null 2>&1")
fd = os.open("/tmp/test_file", os.O_RDONLY)
print("Reading 10,000 bytes one byte at a time...")
for i in range(10000):
os.read(fd, 1) # Very inefficient!
os.close(fd)
print("Finished reading.")
if __name__ == "__main__":
main()
The Investigation
To get a high-level performance summary, use the -c (count) flag with strace:
$ strace -c python3 io_profile.py
Instead of logging individual calls, this command produces a summary table at the end, showing the time and number of calls for each syscall. The output will look something like this:
| % time | calls | syscall |
| 55.03 | 10001 | read |
| 31.03 | 1 | wait4 |
| 8.02 | 187 | newfstatat |
| … | … | … |
The Insight
The summary table immediately exposes the bottleneck. The application made over 10,000 individual read() calls, which accounted for over half of the total time spent in system calls. This pattern of many small reads is a classic performance killer. Armed with this data, a developer can optimize the code to use a larger buffer, drastically reducing the number of system calls and improving performance.
Best Practices and Next Steps
To make strace your go-to debugging companion, keep these tips in mind:
- Filter Your Output: Use
-e trace=...to focus only on relevant syscalls (e.g.,openat,connect,mmap). - Follow Child Processes: If your application forks, use the
-fflag to trace the parent and all its children. - Save for Later: Use
-o filename.txtto save the massive output to a file for careful analysis. - Beware the Overhead:
stracesignificantly slows down an application. Be very cautious about using it on production systems. - Expand Your Toolkit:
straceis just the beginning. The Linux tracing ecosystem includes powerful tools likeltrace(for library calls),perf(for low-overhead performance analysis), andeBPF(for custom, in-kernel tracing).
The next time you face a truly baffling bug, remember to reach for strace. It pulls back the curtain and shows you the truth of what’s really happening on your system.
- Build a Python Chat Server: A Beginner’s Guide to Sockets and Threads
- A Guide to PostgreSQL – How to Optimize Database Performance
- A Guide to Regex – How to Use Regular Expressions with grep
- A Guide to DNF – How to Manage Software Packages in Fedora
- A Beginner’s Guide to Godot – How to Start Developing Video Games
- An Introduction to Ansible – How to Automate Your System Administration
- A Guide to iperf3 – How to Test Your Network Performance