
A Beginner’s Guide to Godot – How to Start Developing Video Games
I've always dreamed of creating my own video games, but for a long time, the complexity of game engines felt like a huge barrier.
Stay updated with the latest tech news, gadgets, and digital trends.

I've always dreamed of creating my own video games, but for a long time, the complexity of game engines felt like a huge barrier.

As a system administrator, I'm always looking for ways to automate repetitive tasks and manage my servers more efficiently.

When I'm setting up a new network or troubleshooting connectivity issues, I often need a reliable way to measure its actual performance.

There are many times when I need to access the graphical desktop of my Linux machine from another computer.

In today's world, having a secure way to connect to my home or office network remotely is essential.

As a developer, I'm always exploring new programming languages to add to my toolkit.

As someone who manages multiple computers, keeping files and backups synchronized used to be a tedious task.

In an age where online privacy is constantly under threat, I believe it's essential for everyone to have tools that can help them protect their digital footprint.
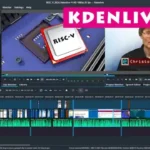
When I first started creating videos, I was looking for a powerful yet accessible video editor that wouldn't break the bank.
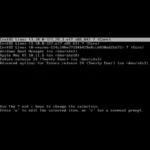
As someone who frequently tests different Linux distributions, I used to have a collection of USB sticks, each with a different live ISO.

As a developer, I've come to rely heavily on container technology to build, ship, and run applications in isolated environments.
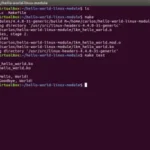
As I delved deeper into the world of Linux, I became fascinated by its core: the kernel.

As a Linux enthusiast, one of the most exciting and empowering projects I've undertaken is creating my own personalized Linux distribution.

When I'm working with Linux, security is always a top priority.
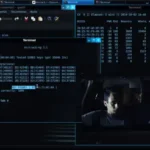
As someone who takes digital security seriously, I believe it's important to understand the tools and techniques that can be used to test network vulnerabilities.