As someone who takes digital security seriously, I believe it’s important to understand the tools and techniques that can be used to test network vulnerabilities. One of the most powerful toolkits for Wi-Fi security assessment is Aircrack-ng. While these tools can be used for malicious purposes, my focus here is on ethical hacking: using them to audit the security of your own network to identify and fix weaknesses.
Table of Contents
Warning: You should only ever use these techniques on a network that you own and have explicit permission to test. Using them on other people’s networks is illegal. This guide is for educational purposes only.
We’ll walk through the basic steps of using the Aircrack-ng suite to capture the necessary data from a WPA/WPA2 network and attempt to crack the password using a dictionary attack.
📡 Step 1: Setting Up Your Wireless Card
The first step is to put your wireless network card into ‘monitor mode’. This allows the card to listen to all the Wi-Fi traffic in the air around you, not just the traffic directed to your computer. I use the `airmon-ng` tool for this.
In the terminal, I first identify my wireless interface name (e.g., `wlan0`) and then run the command to start monitor mode: `sudo airmon-ng start wlan0`. This creates a new monitor interface, often named `wlan0mon`.
👀 Step 2: Capturing Network Traffic with airodump-ng
With my card in monitor mode, the next step is to find my target network and capture the traffic. For this, I use `airodump-ng`. Running `sudo airodump-ng wlan0mon` shows me a list of all the Wi-Fi networks in my vicinity, along with the clients connected to them.
Once I’ve identified my own network from the list, I run a more specific `airodump-ng` command to focus only on that network and save the captured data to a file. The goal here is to capture a WPA handshake, which is the four-way authentication process that occurs when a device connects to the router. This handshake contains the encrypted password that I will try to crack.
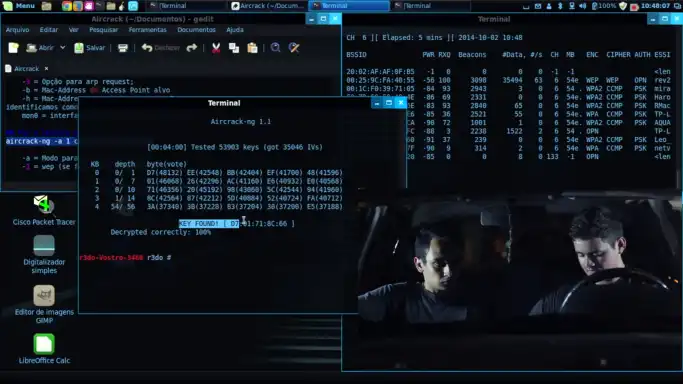
🔑 Step 3: Cracking the Password with aircrack-ng
Once I have successfully captured a handshake, the final step is to use the main tool, `aircrack-ng`, to try and find the password. This tool performs a dictionary attack, which means it rapidly tries every word from a given wordlist to see if it’s the correct password.
The command looks something like this: `aircrack-ng -w /path/to/wordlist.txt captured-file.cap`. I point the tool to my wordlist (a simple text file with one password candidate per line) and the capture file containing the handshake. If the network’s password is in my wordlist, `aircrack-ng` will eventually find it and display it on the screen.
This process demonstrates why using a strong, complex password that is not a common dictionary word is so crucial for Wi-Fi security. For more security tips, check out this guide on using VPNs for anonymity.
- Build a Python Chat Server: A Beginner’s Guide to Sockets and Threads
- A Practical Guide to Strace in Linux: Debugging the Undebuggable
- A Guide to PostgreSQL – How to Optimize Database Performance
- A Guide to Regex – How to Use Regular Expressions with grep
- A Guide to DNF – How to Manage Software Packages in Fedora
- A Beginner’s Guide to Godot – How to Start Developing Video Games
- An Introduction to Ansible – How to Automate Your System Administration